https://www.amazon.com/gp/bestsellers/books/13718/ref=pd_zg_hrsr_books
Month: February 2021
GitHub – marin-m/SongRec: An open-source Shazam client for Linux, written in Rust.
How can I create a keyboard shortcut for highlighting text in LO Writer? – Ask LibreOffice
Highlighting text is not an “action” on text. It is an additional attribute on a character.
To achieve your goal, you must first define a character style with the specific colour selected as Background. Give a name to this style. You can now give it a keyboard shortcut.
This shortcut is not auto-toggling like Ctrl+B or I. I suggest you also associate a keyboard shortcut to character style Default Style so that you can cancel the effect of highlighting from the keyboard.
To show the community your question has been answered, click the ✓ next to the correct answer, and “upvote” by clicking on the ^ arrow of any helpful answers. These are the mechanisms for communicating the quality of the Q&A on this site. Thanks!
Source: How can I create a keyboard shortcut for highlighting text in LO Writer? – Ask LibreOffice
dm-crypt
dm-crypt is a transparent disk encryption subsystem in Linux kernel versions 2.6 and later and in DragonFly BSD. It is part of the device mapper infrastructure, and uses cryptographic routines from the kernel’s Crypto API. Unlike its predecessor cryptoloop, dm-crypt was designed to support advanced modes of operation, such as XTS, LRW and ESSIV (see disk encryption theory for further information), in order to avoid watermarking attacks. In addition to that, dm-crypt also addresses some reliability problems of cryptoloop.
dm-crypt is implemented as a device mapper target and may be stacked on top of other device mapper transformations. It can thus encrypt whole disks (including removable media), partitions, software RAID volumes, logical volumes, as well as files. It appears as a block device, which can be used to back file systems, swap or as an LVM physical volume.
Some Linux distributions support the use of dm-crypt on the root file system. These distributions use initrd to prompt the user to enter a passphrase at the console, or insert a smart card prior to the normal boot process.
Source: dm-crypt – Wikipedia
Using Flatpak on Ubuntu and Other Linux
Source: Using Flatpak on Ubuntu and Other Linux [Complete Guide]
U.FL/IPX IPEX UFL to RP SMA SMA Female Male Antenna WiFi Pigtail Cable ufl ipex 1.13mm RF Cable 15CM|Connectors| – AliExpress

10PCS 2.54mm 40 Pin Stright Female Single Row Pin Header Strip PCB Connector|Integrated Circuits

apt – Failed to add /run/systemd/ask-password to directory watch: No space left on device? – Ask Ubuntu
– The long-term fix is to edit the file /etc/sysctl.conf to include the line:
fs.inotify.max_user_watches=1048576
- reload sysctl.conf with:
#sysctp -pidempotent
FAI – Fully Automatic Installation
FAI is a tool for unattended mass deployment of Linux. It’s a system to install and configure Linux systems and software packages on computers as well as virtual machines, from small labs to large-scale infrastructures like clusters and virtual environments. You can take one or more virgin PC’s, turn on the power, and after a few minutes, the systems are installed, and completely configured to your exact needs, without any interaction necessary.
GitHub – MicrosoftDocs/mslearn-troubleshoot-inbound-network-connectivity-azure-load-balancer: Code samples and resources for learn module “Troubleshoot inbound network connectivity for Azure Load Balancer”
A tcpdump Tutorial with Examples
Let’s start with a basic command that will get us HTTPS traffic:
tcpdump -nnSX port 443
04:45:40.573686 IP 78.149.209.110.27782 > 172.30.0.144.443: Flags [.], ack 278239097, win 28, options [nop,nop,TS val 939752277 ecr 1208058112], length 0 0x0000: 4500 0034 0014 0000 2e06 c005 4e8e d16e E..4........N..n 0x0010: ac1e 0090 6c86 01bb 8e0a b73e 1095 9779 ....l......>...y 0x0020: 8010 001c d202 0000 0101 080a 3803 7b55 ............8.{U 0x0030: 4801 8100
You can get a single packet with -c 1, or n number with -c n.
This showed some HTTPS traffic, with a hex display visible on the right portion of the output (alas, it’s encrypted). Just remember—when in doubt, run the command above with the port you’re interested in, and you should be on your way.
Examples
PacketWizard™ isn’t really trademarked, but it should be.

A PRACTITIONER PREPARING TO RUN TCPDUMP
Now that you are able to get basic traffic, let’s step through numerous examples that you are likely to need during your job in networking, security, or as any type of PacketWizard™.
everything on an interface
Just see what’s going on, by looking at what’s hitting your interface.
Or get all interfaces with -i any.
tcpdump -i eth0
find traffic by ip
One of the most common queries, using host, you can see traffic that’s going to or from 1.1.1.1.
Expression Types:
host, net, and port.
Directions:
src and dst.
Types:
host, net, and port.
Protocols:
tcp, udp, icmp, and many more.
tcpdump host 1.1.1.1
06:20:25.593207 IP 172.30.0.144.39270 > one.one.one.one.domain: 12790+ A? google.com. (28) 06:20:25.594510 IP one.one.one.one.domain > 172.30.0.144.39270: 12790 1/0/0 A 172.217.15.78 (44)
filtering by source and/or destination
If you only want to see traffic in one direction or the other, you can use src and dst.
tcpdump src 1.1.1.1
tcpdump dst 1.0.0.1
finding packets by network
To find packets going to or from a particular network or subnet, use the net option.
You can combine this with the src and dst options as well.
tcpdump net 1.2.3.0/24
get packet contents with hex output
Hex output is useful when you want to see the content of the packets in question, and it’s often best used when you’re isolating a few candidates for closer scrutiny.
tcpdump -c 1 -X icmp
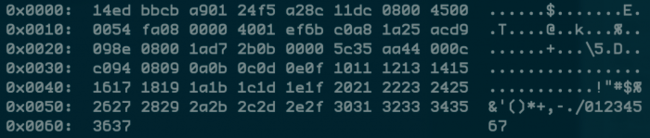
A SINGLE ICMP PACKET VISIBLE IN HEX
tcpdump is the tool everyone should learn as their base for packet analysis.
show traffic related to a specific port
Common Options:
-nn : Don’t resolve hostnames or port names.
-S : Get the entire packet.
-X : Get hex output.
You can find specific port traffic by using the port option followed by the port number.
tcpdump port 3389
tcpdump src port 1025
show traffic of one protocol
If you’re looking for one particular kind of traffic, you can use tcp, udp, icmp, and many others as well.
tcpdump icmp
show only ip6 traffic
You can also find all IP6 traffic using the protocol option.
tcpdump ip6
find traffic using port ranges
You can also use a range of ports to find traffic.
tcpdump portrange 21-23
find traffic based on packet size
If you’re looking for packets of a particular size you can use these options. You can use less, greater, or their associated symbols that you would expect from mathematics.
tcpdump less 32
tcpdump greater 64
tcpdump <= 128
reading / writing captures to a file (pcap)
It’s often useful to save packet captures into a file for analysis in the future. These files are known as PCAP (PEE-cap) files, and they can be processed by hundreds of different applications, including network analyzers, intrusion detection systems, and of course by tcpdump itself. Here we’re writing to a file called capture_file using the -w switch.
tcpdump port 80 -w capture_file
You can read PCAP files by using the -r switch. Note that you can use all the regular commands within tcpdump while reading in a file; you’re only limited by the fact that you can’t capture and process what doesn’t exist in the file already.
tcpdump -r capture_file
advanced
Now that we’ve seen what we can do with the basics through some examples, let’s look at some more advanced stuff.
More options
Here are some additional ways to tweak how you call tcpdump.
-X: Show the packet’s contents in both hex and ascii.-XX: Same as-X, but also shows the ethernet header.-D: Show the list of available interfaces-l: Line-readable output (for viewing as you save, or sending to other commands)-q: Be less verbose (more quiet) with your output.-t: Give human-readable timestamp output.-tttt: Give maximally human-readable timestamp output.-i eth0: Listen on the eth0 interface.-vv: Verbose output (more v’s gives more output).-c: Only get x number of packets and then stop.-s: Define the snaplength (size) of the capture in bytes. Use-s0to get everything, unless you are intentionally capturing less.-S: Print absolute sequence numbers.-e: Get the ethernet header as well.-q: Show less protocol information.-E: Decrypt IPSEC traffic by providing an encryption key.
It’s All About the Combinations
Being able to do these various things individually is powerful, but the real magic of tcpdump comes from the ability to combine options in creative ways in order to isolate exactly what you’re looking for. There are three ways to do combinations, and if you’ve studied programming at all they’ll be pretty familiar to you.
- AND
andor&& - OR
oror|| - EXCEPT
notor!
raw output view
Use this combination to see verbose output, with no resolution of hostnames or port numbers, using absolute sequence numbers, and showing human-readable timestamps.
tcpdump -ttnnvvS
Here are some examples of combined commands.
from specific ip and destined for a specific port
Let’s find all traffic from 10.5.2.3 going to any host on port 3389.
tcpdump -nnvvS src 10.5.2.3 and dst port 3389
from one network to another
Let’s look for all traffic coming from 192.168.x.x and going to the 10.x or 172.16.x.x networks, and we’re showing hex output with no hostname resolution and one level of extra verbosity.
tcpdump -nvX src net 192.168.0.0/16 and dst net 10.0.0.0/8 or 172.16.0.0/16
non icmp traffic going to a specific ip
This will show us all traffic going to 192.168.0.2 that is not ICMP.
tcpdump dst 192.168.0.2 and src net and not icmp
traffic from a host that isn’t on a specific port
This will show us all traffic from a host that isn’t SSH traffic (assuming default port usage).
tcpdump -vv src mars and not dst port 22
As you can see, you can build queries to find just about anything you need. The key is to first figure out precisely what you’re looking for and then to build the syntax to isolate that specific type of traffic.
Keep in mind that when you’re building complex queries you might have to group your options using single quotes. Single quotes are used in order to tell tcpdump to ignore certain special characters—in this case below the “( )” brackets. This same technique can be used to group using other expressions such as host, port, net, etc.
tcpdump ‘src 10.0.2.4 and (dst port 3389 or 22)’
isolate tcp flags
Source: A tcpdump Tutorial with Examples — 50 Ways to Isolate Traffic | Daniel Miessler