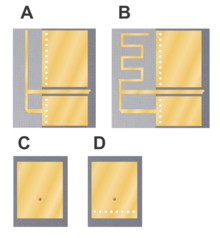
An inverted-F antenna is a type of antenna used in wireless communication, mainly at UHF and microwave frequencies. It consists of a monopole antenna running parallel to a ground plane and grounded at one end. The antenna is fed from an intermediate point a distance from the grounded end. The design has two advantages over a simple monopole: the antenna is shorter and more compact, allowing it to be contained within the case of the mobile device, and it can be impedance matched to the feed circuit by the designer, allowing it to radiate power efficiently, without the need for extraneous matching components.
The inverted-F antenna was first conceived in the 1950s as a bent-wire antenna. However, its most widespread use is as a planar inverted-F antenna (PIFA) in mobile wireless devices for its space saving properties. PIFAs can be printed using the microstrip format, a widely used technology that allows printed RF components to be manufactured as part of the same printed circuit board used to mount other components.
PIFAs are a variant of the patch antenna. Many variants of this, and other forms of the inverted-F, exist that implement wideband or multi-band antennas. Techniques include coupled resonators and the addition of slots.
Source: Inverted-F antenna – Wikipedia