Combining two different packages for a security solution can be dangerous. This is the PuTTY-only way to do it, only using software from the PuTTY site.
You should first use PuTTYgen to create a key pair, then install the private key in PuTTY, and copy the public key to the remote site. Here is how you do this.
Download PuTTYgen, and execute it to generate a SSH2-RSA key. I’d use at least 4098 bits. Click the Generate button, move the mouse around, until the key pair is generated.
Once it’s generated, your screen will look like this: 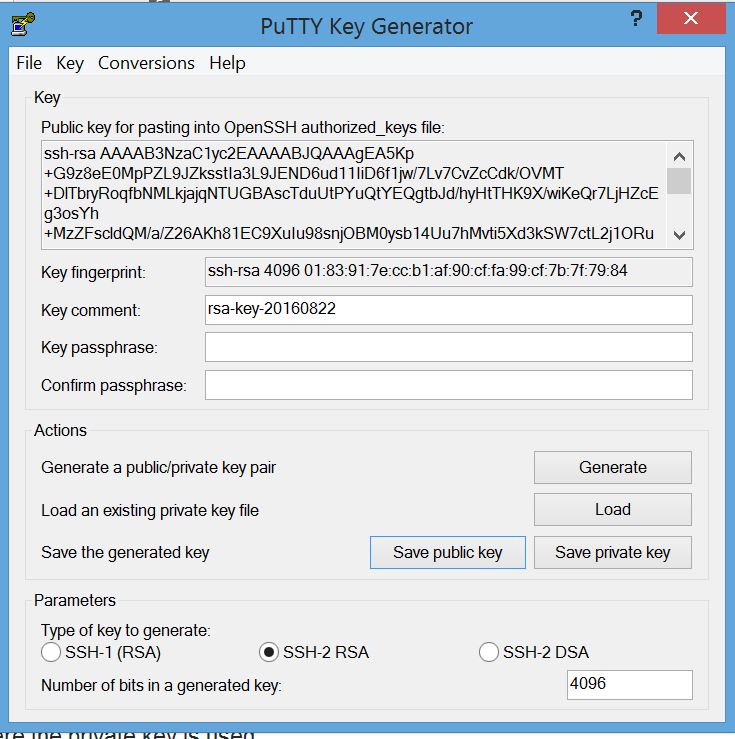
Describe the account in the “Key Comment” field. Then save the private key in one file, and the public key in another file.
Your public key will look like this:
---- BEGIN SSH2 PUBLIC KEY ----
Comment: "rsa-key-20160822"
AAAAB3NzaC1yc2EAAAABJQAAAgEA5Kp+G9z8eE0MpPZL9JZksstIa3L9JEND6ud1
1IiD6f1jw/7Lv7CvZcCdk/OVMT+DlTbryRoqfbNMLkjajqNTUGBAscTduUtPYuQt
YEQgtbJd/hyHtTHK9X/wiKeQr7LjHZcEg3osYh+MzZFscldQM/a/Z26AKh81EC9X
uIu98snjOBM0ysb14Uu7hMvti5Xd3kSW7ctL2j1ORuRgZX6LHihaezvsBFI5S/lZ
4v/yxymRKQnyV6OkMNMXESJpXh3cTMIIGtDJtbbYvh5Qs0f3O1fMiQYyz2MjGphd
zBihq85a1SHx0LBk31342HsCiM4el//Zkicmjmy0qYGShmzh1kfZBKiBs+xN4tBE
yjRNYhuMGP2zgpr9P/FO1buYdLah5ab3rubB5VbbRP9qmaP2cesJS/N91luc099g
Z+CgeBVIiRr1EYTE8TqsSBdvmu3zCuQgDVcSAoubfxjM4sm3Lb6i4k4DJmF57J6T
rcyrSIP9H/PDuBuYoOfSBKies6bJTHi9zW2/upHqNlqa2+PNY64hbq2uSQoKZl1S
xwSCvpbsYj5bGPQUGs+6AHkm9DALrXD8TX/ivQ+IsWEV3wnXeA4I1xfnodfXdhwn
ybcAlqNrE/wKb3/wGWdf3d8cu+mJrJiP1JitBbd4dzYM0bS42UVfexWwQSegDHaw
Aby0MW0=
---- END SSH2 PUBLIC KEY ----
You have to edit this to a form that is suitable for your remote site. Let’s assume it’s a Linux machine using ssh.
Edit the file so it has three fields:
- The first should say “ssh-rsa”
- The second should be your public key all on one line with no spaces.
- The third is a comment – which can correspond to your key comment field.
So it should look like this when done
ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAgEA5Kp+G9z8eE0MpPZL9JZksstIa3L9JEND6ud11IiD6f1jw/7Lv7CvZcCdkOVMT+DlTbryRoqfbNMLkjajqNTUGBAscTduUtPYuQtYEQgtbJdhyHtTHK9XwiKeQr7LjHZcEg3osYh+MzZFscldQMaZ26AKh81EC9XuIu98snjOBM0ysb14Uu7hMvti5Xd3kSW7ctL2j1ORuRgZX6LHihaezvsBFI5SlZ4vyxymRKQnyV6OkMNMXESJpXh3cTMIIGtDJtbbYvh5Qs0f3O1fMiQYyz2MjGphdzBihq85a1SHx0LBk31342HsCiM4elZkicmjmy0qYGShmzh1kfZBKiBs+xN4tBEyjRNYhuMGP2zgpr9PFO1buYdLah5ab3rubB5VbbRP9qmaP2cesJSN91luc099gZ+CgeBVIiRr1EYTE8TqsSBdvmu3zCuQgDVcSAoubfxjM4sm3Lb6i4k4DJmF57J6TrcyrSIP9HPDuBuYoOfSBKies6bJTHi9zW2upHqNlqa2+PNY64hbq2uSQoKZl1SxwSCvpbsYj5bGPQUGs+6AHkm9DALrXD8TXivQ+IsWEV3wnXeA4I1xfnodfXdhwnybcAlqNrEwKb3wGWdf3d8cu+mJrJiP1JitBbd4dzYM0bS42UVfexWwQSegDHawAby0MW0= rsa-key-20160822
Personally, I would copy the file over to the Linux machine, and then edit it, because editors like vim are much more tolerant of long lines. I’d use the ‘J’ command to join two lines, then search for spaces and delete the spaces between the lines. When I copied this file over to Windows, the system insisted on splitting the single long line into multiple lines with “\” between the lines. Yuck. To continue…
Log into the remote machine, and copy/edit, then append the public key into the ~/.ssh/authorized_keys file in the same format as the other keys. It should be a single line. There should be three fields on a single line. The first says “ssh-rsa”. The second is the key which should end with the characters “=” the third field is optional, and will contain what you put in the Key Comment field.
If this is the first time you have created the ~/.ssh/authorized_keys file, make sure the directory and file are not group or world readable.
Once this is done, then you have to create a PuTTY session where the private key is used.
In the PuTTY session, go to Connection=>SSH=>Auth and click browse and select where you stored your private key “It’s a *.ppk” file. 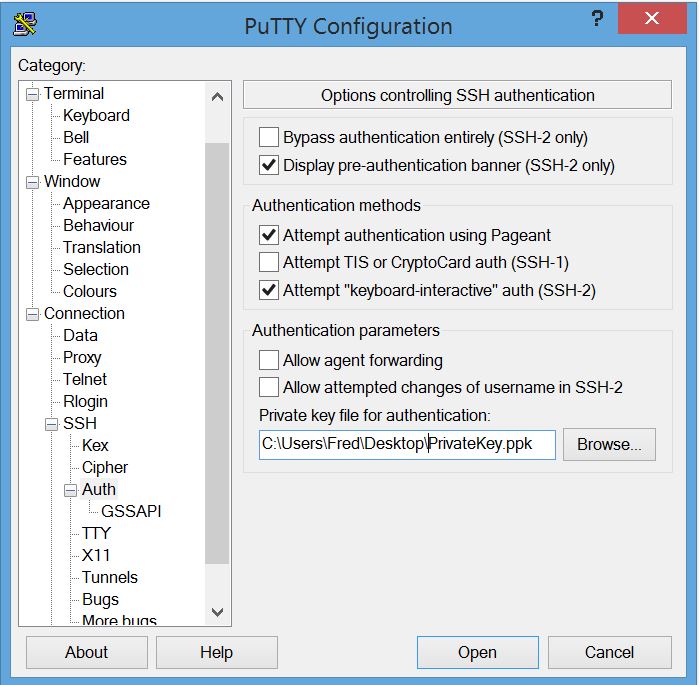
Then save this session (I’m assuming you also set up the account, IP address, etc.).
Once this is done, you just have to select the session, and you are logged in.
A more secure way is to store your private key in an encrypted file, using a passphrase. Then use Pageant to manage your passphrase. That way the private key is always encrypted, and you only have to type in a passphrase once in a while.
Source: Is there a way to “auto login” in PuTTY with a password? – Super User