\sloppy
1 Cooperative Diversity without Temporal Diversity
1.1 System Model
1.1.1 Equivalent Channel Models
For direct transmission, our baseline for comparison, we model the channel as:
for say, n = 1, 2, ...N ⁄ 2, where xs[n] is the source transmitted signal and yd[n] is the destination received signal.
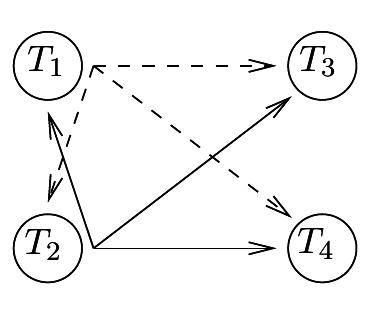
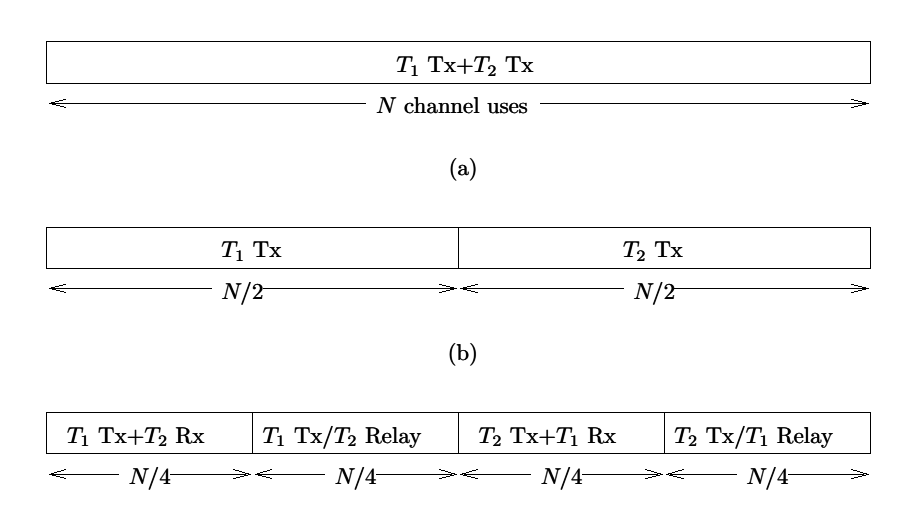
the other terminal transmits for n = N ⁄ 2 + 1, ..., N as 1.2↑ depicts.
For cooperative diversity transmission, we model the channel during the first half of the blocks as
for say, \mathchoicen = 1, ..., N ⁄ 4n = 1, ..., N ⁄ 4n = 1, ..., N ⁄ 4n = 1, ..., N ⁄ 4 where xs[n] is the source transmitted signal and yr[n] and yd[n] are the relay and destination received signals, respectively. For the second half of the block, we model the received signal as:
for \mathchoicen = N ⁄ 4 + 1, .., N ⁄ 2n = N ⁄ 4 + 1, .., N ⁄ 2n = N ⁄ 4 + 1, .., N ⁄ 2n = N ⁄ 4 + 1, .., N ⁄ 2, where xr[n] is the relay transmitted signal and yd[n] is the destination received signal.
A similar setup is employed in the second half of the block, with the roles of the source and relay reversed, as 1.2↑ depicts. While again half the degrees of freedom are allocated to each source terminal for transmission to its destination, only a quarter of the degrees of freedom are available for communication to its relay.
In 1.1↑-1.4↑ ai, j captures the effects of path-loss, shadowing, and frequency non-selective fading, and zj[n] captures the effects of receiver noise and other forms of interference in the system, where i ∈ {s, r} and j ∈ {r, d}. Statistically, we model ai, j as zero-mean, independent, circularly-symmetric complex gaussian random variables with variances σ2i, j so that the magnitudes |ai, j| are Rayleigh distributed (|aij|2 are exponentially distributed wiht mean σ2i, j) and phases ∠ai, j are uniformly distributed on [0, 2π]. Furthermorre, we model zj[n] as zeropmean mutually independent, circularly-symmetric, complex Gaussian random sequences with variance N0
1.1.2 Parametrization
SNR≜(2Pc)/(No⋅W) = (P)/(N0) is SNR without fading.
Spectral efficiency
R≜2r ⁄ W b ⁄ s ⁄ Hz
SNRnorm≜(SNR)/(2R − 1) Rnorm≜(R)/(log(1 + SNRσ2s, d(s)))
1.2 Cooperative Transmission Protocols
1.2.1 Fixed Protocols
1.2.1.1 Amplify-and Forward Transmission
For amplify-and-forward transmission, the appropriate channel model is 1.2↑-1.4↑. The source terminal transmits its information as xs[n] , say, for n = 1, ..., N ⁄ 4. During this interval, the relay processes yr[n], and relays the information by transmitting
for n = N ⁄ 4 + 1, ..., N ⁄ 2. To remain within its power constraint (with high probability), an amplify relay must use gain:
β ≤ √((P)/(|as, r|2P + N0))
where we allow the amplifier gain to depend upon the fading coefficient as, r between the source and relay, which the relay estimates to high accuracy. This transmission scheme can be viewed as repetition coding from two separate transmitters, except that the relay transmitter amplifies its own receiver noise. The destination can decode its received signal yd[n] for n = 1, ..., N ⁄ 2 by first appropriately combining the signals form the two subblocks using a suitably designed matched-fiter (maximum-ratio combiner).
1.2.1.2 Decode and Forward Transmission
For decode-and forward transmission, the appropriate channel model is again 1.2↑-1.4↑. the source terminal transmits its information as xs[n] , say , for n = 0, ..., N ⁄ 4. During this interva, the relay processes yr[n] by decoding an estimate x̂s[n] of the source transmitted signal.
Under a repetition coded scheme, the relay transmits the signal
xr[n] = x̂s[n − N ⁄ 4]
for n = N ⁄ 4 + 1, ...N ⁄ 2 .
Decoding at the relay can take on variety of forms. For example, the relay might fully decode the source message by estimating the source code-word, or it might employ symbol-by-symbol decoding and allow the destination to perform full decoding. These options allow for trading off performance and complexity at the relay terminal. Beacuse the performance of symbol-bysymbol decoding varies with the choice of coding and modulatio, we focus on full decoding in the sewuel; symbol-by-symbol decoding of binary transmisssions has been treated from uncodded perspecitve in [1].
2 Appendix C: Mutual Information Calculations
2.1 Amplify-and-forward Mutual Information
In this section, we compute the maximum average mutual information for amplify and forward transmission. We write the equvalent channel 1.2↑-1.4↑, with relay processing 1.5↑, in vector form as:
yd[n] = as, dxs + zd[n]; yr[n] = as, rxs[n] + zr[n]; xr[n] = β⋅yr[n − N ⁄ 4] = β⋅as, rxs[n − N ⁄ 4] + β⋅zr[n − N ⁄ 4];
yd[n] = ar, d(s)xr[n] + zd[n]; yd[n] = ar, d(s)β⋅as, rxs[n − N ⁄ 4] + ar, d(s)⋅β⋅zr[n − N ⁄ 4] + zd[n] yd[n + N ⁄ 4] = ar, d(s)β⋅as, rxs[n] + ar, d(s)⋅β⋅zr[n] + zd[n + N ⁄ 4]
⎡⎢⎣
yd[n]
yd[n + N ⁄ 4]
⎤⎥⎦ = ⎡⎢⎣
as, d(s)
ar, d(s)β⋅as, r
⎤⎥⎦xs[n] + ⎡⎢⎣
0
1
0
ar, d(s)β
0
1
⎤⎥⎦⋅⎡⎢⎢⎢⎣
zr[n]
zd[n]
zd[n + N ⁄ 4]
⎤⎥⎥⎥⎦
where the source signal has power constraint E[xs] ≤ Ps, and relay amplifier has constraint:
β ≤ √((Pr)/(|as, r|2Ps + Nr))
and the noise has covariance E[zzT] = diag(Nr, Nd, Nd)
E⎡⎢⎢⎢⎣⎡⎢⎢⎢⎣
z1
z2
z3
⎤⎥⎥⎥⎦⋅[
z1
z2
z3
]⎤⎥⎥⎥⎦ = E⎡⎢⎢⎢⎣⎡⎢⎢⎢⎣
z21
z1z2
z1z3
z2z1
z22
z2z3
z1z3
z2z3
z23
⎤⎥⎥⎥⎦⎤⎥⎥⎥⎦ = ⎡⎢⎢⎢⎣
Ez21
0
0
0
Ez22
0
0
0
Ez23
⎤⎥⎥⎥⎦ = ⎡⎢⎢⎢⎣
Nr
0
0
0
Nd
0
0
0
Nd
⎤⎥⎥⎥⎦
Note that we determine the mutual information for arbitrary transmit powers and noise levels, even though we utilize the result only for the symmetric case. Since the channel is memoryless, the average mutual information satisfies
IAF ≤ I(xs;yd) ≤ logdet(I + (PsAAT)⋅(B⋅E[z⋅zT]⋅BT) − 1)
A⋅AT = ⎡⎢⎣
as, d(s)
ar, d(s)β⋅as, r
⎤⎥⎦⋅⎡⎢⎣
as, d(s)
ar, d(s)β⋅as, r
⎤⎥⎦† = ⎡⎢⎣
as, d(s)as, d(s)
as, d(s)ar, d(s)β as, r
ar, d(s)β as, ras, d(s)
ar, d(s)β as, rar, d(s)β as, r
⎤⎥⎦ = ⎡⎢⎣
|as, d(s)|2
as, d(s)ar, d(s)β as, r
ar, d(s)β as, ras, d(s)
|ar, d(s)β as, r|2
⎤⎥⎦
†-conjugate transpose
B⋅E[z⋅z†]⋅B† = ⎡⎢⎣
0
1
0
ar, d(s)β
0
1
⎤⎥⎦⋅⎡⎢⎢⎢⎣
Nr
0
0
0
Nd
0
0
0
Nd
⎤⎥⎥⎥⎦⋅⎡⎢⎣
0
1
0
ar, d(s)β
0
1
⎤⎥⎦† = ⎡⎢⎣
Nd
0
0
ar, d(s)β Nrar, d(s)β + Nd
⎤⎥⎦
det(I2 + (PsAAT)⋅(B⋅E[z⋅zT]⋅BT) − 1) = det⎛⎜⎝⎡⎢⎣
1
0
0
1
⎤⎥⎦ + Ps⎡⎢⎣
|as, d(s)|2
as, d(s)ar, d(s)β as, r
ar, d(s)β as, ras, d(s)
|ar, d(s)β as, r|2
⎤⎥⎦⋅⎡⎢⎣
Nd
0
0
ar, d(s)β Nrar, d(s)β + Nr
⎤⎥⎦⎞⎟⎠
= det⎛⎜⎝⎡⎢⎣
1 + (Ps(|as, d(s)|)2)/(Nd)
(Psas, d(s)ar, d(s)βas, r)/(Nrar, d(s)β ar, d(s)β + Nd)
(Psar, d(s)β as, ras, d(s))/(Nd)
1 + (Ps(|ar, d(s)β as, r|)2)/(Nrar, d(s)β ar, d(s)β + Nd)
⎤⎥⎦⎞⎟⎠ = 1 + (Ps⋅|as, d(s)|2)/(Nd) + (Ps⋅|ar, d(s)β as, r|2)/(Nrar, d(s)β ar, d(s)β + Nd) = 1 + (Ps⋅|as, d(s)|2)/(Nd) + (Ps⋅|ar, d(s)β as, r|2)/(Nr|ar, d(s)β|2 + Nd)
β ≤ √((Pr)/(|as, r|2Ps + Nr)) β2 ≤ (Pr)/(|as, r|2Ps + Nr)
1 + (Ps⋅|as, d(s)|2)/(Nd) + (Ps⋅|ar, d(s)β as, r|2)/(Nr|ar, d(s)|2⋅(Pr)/(|as, r|2Ps + Nr) + Nd) = 1 + SNRs, d(s)⋅|as, d(s)|2 + (Ps⋅|ar, d(s)β as, r|2)/(|ar, d(s)|2⋅(Pr)/(|as, r|2Ps ⁄ Nr + 1) + Nd) = 1 + SNRs, d(s)⋅|as, d(s)|2 + (Ps⋅|ar, d(s)β as, r|2)/(|ar, d(s)|2⋅(Pr)/(|as, r|2SNRs, r + 1) + Nd) =
= 1 + SNRs, d(s)⋅|as, d(s)|2 + (Ps⋅|ar, d(s)β as, r|2)/(Nd⎛⎝|ar, d(s)|2⋅(Pr ⁄ Nd)/(|as, r|2SNRs, r + 1) + 1⎞⎠) = 1 + SNRs, d(s)⋅|as, d(s)|2 + (Ps ⁄ Nd⋅|ar, d(s)as, r|2)/(⎛⎝|ar, d(s)|2⋅(SNRr, d(s))/(|as, r|2SNRs, r + 1) + 1⎞⎠)⋅(Pr)/(|as, r|2Ps + Nr)
= 1 + SNRs, d(s)⋅|as, d(s)|2 + (Ps ⁄ Nd⋅|ar, d(s)as, r|2)/(⎛⎝|ar, d(s)|2⋅(SNRr, d(s))/(|as, r|2SNRs, r + 1) + 1⎞⎠)⋅(Pr ⁄ Nr)/(|as, r|2Ps ⁄ Nr + 1) = 1 + SNRs, d(s)⋅|as, d(s)|2 + (Ps ⁄ Nr⋅|ar, d(s)as, r|2)/(⎛⎝|ar, d(s)|2⋅(SNRr, d(s))/(|as, r|2SNRs, r + 1) + 1⎞⎠)⋅(Pr ⁄ Nd)/(|as, r|2SNRs, r + 1) =
= 1 + SNRs, d(s)⋅|as, d(s)|2 + (SNRs, r⋅|ar, d(s)as, r|2⋅SNRr, d(s))/((|ar, d(s)|2⋅SNRr, d(s) + |as, r|2SNRs, r + 1)) = 1 + SNRs, d(s)⋅|as, d(s)|2 + (|as, r|2⋅SNRs, r⋅|ar, d(s)|2⋅SNRr, d(s))/(|as, r|2SNRs, r + |ar, d(s)|2⋅SNRr, d(s) + 1) =
= 1 + SNRs, d(s)⋅|as, d(s)|2 + f(|as, r|2⋅SNRs, r, |ar, d(s)|2⋅SNRr, d(s))
f(x, y)≜(x⋅y)/(x + y)
yd[n] = as, dxs + zd[n]; yr[n] = as, rxs[n] + zr[n]; xr[n] = β⋅yr[n − N ⁄ 4] = β⋅as, rxs[n − N ⁄ 4] + β⋅zr[n − N ⁄ 4];
I(xs;yd) = I(Xs;Yd’, Yd’’) Yd’ = as, dXs + Zd \mathchoiceYd’’Yd’’Yd’’Yd’’ = ardXr + Zd = ard⋅(β⋅asrXs + β⋅Zr) + Zd = \mathchoiceard⋅β⋅asrXs + ard⋅β⋅Zr + Zdard⋅β⋅asrXs + ard⋅β⋅Zr + Zdard⋅β⋅asrXs + ard⋅β⋅Zr + Zdard⋅β⋅asrXs + ard⋅β⋅Zr + Zd
Y3’ = a31X1 + Z3 \mathchoiceY3’’Y3’’Y3’’Y3’’ = a32X2 + Z3 = \mathchoicea32⋅β⋅a31⋅X1 + a32⋅β⋅Z2 + Z3a32⋅β⋅a31⋅X1 + a32⋅β⋅Z2 + Z3a32⋅β⋅a31⋅X1 + a32⋅β⋅Z2 + Z3a32⋅β⋅a31⋅X1 + a32⋅β⋅Z2 + Z3 Y2 = a21X1 + Z2
β = √((P)/(a221P + 1)) = √((P)/(S21 + 1)) =
C ≥ maxp(x1)p(ŷ2|y2)min{I(X1;Y3’) − I(Y2;Ŷ2|X1Y3’) + C0, I(X1;Ŷ2, Y3’)}
C ≥ maxp(x1)p(ŷ2|y2)min{I(X1;Y3’) − I(Y2;Ŷ2|X1Y3’) + C0, I(X1;Ŷ2, Y3’)}
maxp(x1)p(x2)min{I(X1;Y3’) + I(X2;Y3’’), I(X1;Y2, Y3’)}
I(X1;Y3’) = H(Y3’) − H(Y3’|X1) = (1)/(2)log(S31 + 1)
I(X2;Y3’’) = H(Y3’’) − H(Y3’’|X2) = (1)/(2)log(S32 + 1)
I(X2;Y3’’) = H(Y3’’) − H(Y3’’|X2) = (1)/(2)log(2πe)⋅(a232β2a231P + a232β2 + 1) − (1)/(2)log(2πe) = (1)/(2)log(a232β2a231P + a232β2 + 1)
I(X1;Y2, Y3’) = H(Y2Y3’) − H(Y2Y3’|X1) = H(Y2) + H(Y3’|Y2) − H(Y2|X1) − H(Y3’|Y2X1) =
≤ (1)/(2)log(2πe)(S21 + 1) + (1)/(2)log(2πe)⎛⎝E[Y’23] − (E2[Y’3⋅Y2])/(E[Y22])⎞⎠ − (1)/(2)⋅log(2πe) − (1)/(2)⋅log(2πe) =
= (1)/(2)log(S21 + 1) + (1)/(2)log⎛⎝S31 + 1 − (E2[(a31X1 + Z3)⋅(a21X1 + Z3)])/(E[Y22])⎞⎠ = (1)/(2)log(S21 + 1) + (1)/(2)log⎛⎝S31 + 1 − (a231a221⋅E2[X21])/(S21 + 1)⎞⎠ =
= (1)/(2)log(S21 + 1) + (1)/(2)log⎛⎝S31 + 1 − (S21S31)/(S21 + 1)⎞⎠ =
maxp(x1)p(x2)min⎧⎩(1)/(2)log(S31 + 1) + (1)/(2)log(a232β2a231P + a232β2 + 1), (1)/(2)log(S21 + 1) + (1)/(2)log⎛⎝S31 + 1 − (S21S31)/(S21 + 1)⎞⎠⎫⎭
(1)/(2)log(S31 + 1)⋅(a232β2a231P + a232β2 + 1) = (1)/(2)log(S21 + 1)⋅⎛⎝S31 + 1 − (S21S31)/(S21 + 1)⎞⎠ (1)/(2)log(S31 + 1)⋅⎛⎝a232⋅(P)/(S21 + 1)⋅a231P + a232⋅(P)/(S21 + 1) + 1⎞⎠ = (1)/(2)log(S21 + 1)⋅⎛⎝S31 + 1 − (S21S31)/(S21 + 1)⎞⎠
min⎧⎩(1)/(2)log(S31 + 1)⋅⎛⎝(S32⋅S31)/(S21 + 1) + (S32)/(S21 + 1) + 1⎞⎠, (1)/(2)log(S21 + 1)⋅⎛⎝S31 + 1 − (S21S31)/(S21 + 1)⎞⎠⎫⎭
(S21 + 1)⋅⎛⎝S31 + 1 − (S21S31)/(S21 + 1)⎞⎠ = ((S31 + 1)(S21 + 1) − S21S31) = S31S21 + S21 + S31 + 1 − S21S31 = 1 + S31 + S21
Expand[(S31 + 1)(S21 + 1)] = S31S21 + S21 + S31 + 1
(S31 + 1)⋅⎛⎝(S32⋅S31)/(S21 + 1) + (S32)/(S21 + 1) + 1⎞⎠ = (S31 + 1)⋅⎛⎝(S32⋅S31 + S32 + S21 + 1)/(S21 + 1)⎞⎠ = 1 + S31 + (S32(S31 + 1)2)/(S21 + 1)
β = √((P)/(a221P + 1)) = √((P)/(S21 + 1)) =
C ≥ maxp(x1)p(ŷ2|y2)min{I(X1;Y3’) − I(Y2;Ŷ2|X1Y3’) + C0, I(X1;Ŷ2, Y3’)}
C ≥ maxp(x1)p(ŷ2|y2)min{I(X1;Y3’) − I(Y2;Ŷ2|X1Y3’) + C0, I(X1;Ŷ2, Y3’)}
maxp(x1)p(x2)min{I(X1;Y3’) + I(X2;Y3’’), I(X1;Y2, Y3’)}
I(X1;Y3’) = H(Y3’) − H(Y3’|X1) = (1)/(2)log(S31 + 1)
I(X2;Y3’’) = H(Y3’’) − H(Y3’’|X2) = (1)/(2)log(S32 + 1)
I(X2;Y3’’) = H(Y3’’) − H(Y3’’|X2) = (1)/(2)log(2πe)⋅(a232β2a231P + a232β2 + 1) − (1)/(2)log(2πe) = (1)/(2)log(a232β2a231P + a232β2 + 1)
I(X1;Y2, Y3’) = H(Y2Y3’) − H(Y2Y3’|X1) = H(Y2) + H(Y3’|Y2) − H(Y2|X1) − H(Y3’|Y2X1) =
≤ (1)/(2)log(2πe)(S21 + 1) + (1)/(2)log(2πe)⎛⎝E[Y’23] − (E2[Y’3⋅Y2])/(E[Y22])⎞⎠ − (1)/(2)⋅log(2πe) − (1)/(2)⋅log(2πe) =
= (1)/(2)log(S21 + 1) + (1)/(2)log⎛⎝S31 + 1 − (E2[(a31X1 + Z3)⋅(a21X1 + Z3)])/(E[Y22])⎞⎠ = (1)/(2)log(S21 + 1) + (1)/(2)log⎛⎝S31 + 1 − (a231a221⋅E2[X21])/(S21 + 1)⎞⎠ =
= (1)/(2)log(S21 + 1) + (1)/(2)log⎛⎝S31 + 1 − (S21S31)/(S21 + 1)⎞⎠ =
maxp(x1)p(x2)min⎧⎩(1)/(2)log(S31 + 1) + (1)/(2)log(a232β2a231P + a232β2 + 1), (1)/(2)log(S21 + 1) + (1)/(2)log⎛⎝S31 + 1 − (S21S31)/(S21 + 1)⎞⎠⎫⎭
(1)/(2)log(S31 + 1)⋅(a232β2a231P + a232β2 + 1) = (1)/(2)log(S21 + 1)⋅⎛⎝S31 + 1 − (S21S31)/(S21 + 1)⎞⎠ (1)/(2)log(S31 + 1)⋅⎛⎝a232⋅(P)/(S21 + 1)⋅a231P + a232⋅(P)/(S21 + 1) + 1⎞⎠ = (1)/(2)log(S21 + 1)⋅⎛⎝S31 + 1 − (S21S31)/(S21 + 1)⎞⎠
min⎧⎩(1)/(2)log(S31 + 1)⋅⎛⎝(S32⋅S31)/(S21 + 1) + (S32)/(S21 + 1) + 1⎞⎠, (1)/(2)log(S21 + 1)⋅⎛⎝S31 + 1 − (S21S31)/(S21 + 1)⎞⎠⎫⎭
(S21 + 1)⋅⎛⎝S31 + 1 − (S21S31)/(S21 + 1)⎞⎠ = ((S31 + 1)(S21 + 1) − S21S31) = S31S21 + S21 + S31 + 1 − S21S31 = 1 + S31 + S21
Expand[(S31 + 1)(S21 + 1)] = S31S21 + S21 + S31 + 1
(S31 + 1)⋅⎛⎝(S32⋅S31)/(S21 + 1) + (S32)/(S21 + 1) + 1⎞⎠ = (S31 + 1)⋅⎛⎝(S32⋅S31 + S32 + S21 + 1)/(S21 + 1)⎞⎠ = 1 + S31 + (S32(S31 + 1)2)/(S21 + 1)
C ≤ maxp(x1)p(x2)min{I(X1;Y3’) + I(X2;Y3’’), I(X1;Y2, Y3’)}
y3 = g31x1 + g32x2 + z3 y2 = g21x1 + z2 z3 ~ N(0, 1) z2 ~ N(0, 1)
x2 = √((P)/(S21 + 1))y2 = g21√((P2)/(S21 + 1))x1 + √((P2)/(g221P1 + 1))z2 y3 = g31x1 + g32x2 + z3 = g31x1 + g32⋅g21⋅√((P2)/(g221P1 + 1))x1 + g32⋅√((P2)/(g221P1 + 1))z2 + z3 =
I(X1;Y3) = h(Y3) − h(Y3|X1) = h(Y) − h(g31x1 + g32⋅g21⋅√((P2)/(g221P1 + 1))x1 + g32⋅√((P2)/(g221P1 + 1))z2 + z3|X1) =
= h(g31x1 + g32⋅g21⋅√((P2)/(g221P1 + 1))x1 + g32⋅√((P2)/(g221P1 + 1))z2 + z3) − h(g32√((P2)/(g221P1 + 1))z2 + z3) =
= (1)/(2)log2πe⎛⎝g231P + g232⋅g221⋅(P2)/(g221P1 + 1)⋅P1 + g232⋅(P2)/(g221P1 + 1) + 1⎞⎠ − (1)/(2)log2πe⋅⎛⎝g232(P2)/(g221P1 + 1) + 1⎞⎠ =
= (1)/(2)log(⎛⎝g231P + g232⋅g221⋅(P2)/(g221P1 + 1)⋅P1 + \mathchoiceg232⋅(P2)/(g221P1 + 1) + 1g232⋅(P2)/(g221P1 + 1) + 1g232⋅(P2)/(g221P1 + 1) + 1g232⋅(P2)/(g221P1 + 1) + 1⎞⎠)/(⎛⎝g232(P2)/(g221P1 + 1) + 1⎞⎠) = (1)/(2)log⎛⎜⎜⎝1 + (g231P + g232⋅g221⋅(P2)/(g221P1 + 1)⋅P1)/(⎛⎝g232(P2)/(g221P1 + 1) + 1⎞⎠)⎞⎟⎟⎠
(1)/(2)log⎛⎜⎜⎝1 + (S31 + (S32⋅S21)/(S21 + 1))/(⎛⎝(S32)/(S21 + 1) + 1⎞⎠)⎞⎟⎟⎠ = \mathchoice(1)/(2)log⎛⎝1 + (S31(S21 + 1) + S32⋅S21)/(S21 + S31 + 1)⎞⎠(1)/(2)log⎛⎝1 + (S31(S21 + 1) + S32⋅S21)/(S21 + S31 + 1)⎞⎠(1)/(2)log⎛⎝1 + (S31(S21 + 1) + S32⋅S21)/(S21 + S31 + 1)⎞⎠(1)/(2)log⎛⎝1 + (S31(S21 + 1) + S32⋅S21)/(S21 + S31 + 1)⎞⎠ = \mathchoice(1)/(2)log⎛⎝1 + ((S31 + S32)S21 + S31)/(S21 + S31 + 1)⎞⎠(1)/(2)log⎛⎝1 + ((S31 + S32)S21 + S31)/(S21 + S31 + 1)⎞⎠(1)/(2)log⎛⎝1 + ((S31 + S32)S21 + S31)/(S21 + S31 + 1)⎞⎠(1)/(2)log⎛⎝1 + ((S31 + S32)S21 + S31)/(S21 + S31 + 1)⎞⎠
(S31S21 + S32 + S32S21)/(S21 + S31 + 1) = (S31S21 + ⎛⎝\cancelto0(S32)/(S21) + S32⎞⎠⋅S21)/(S21 + S31 + 1) = (S31S21 + S32⋅S21)/(S21 + S31 + 1) = ((S31 + S32)⋅S21)/(S21 + S31 + 1)
1. Прочитај го чланакот [1] имаат прикажано како се прави maximum-ratio combiner.
2. Помини го Appendix A од докторската на Laneman. Површно го поминав. Истите концепти се од EIT и NIT но може Laneman додал нешто интересно. Обично има многу добри објаснувања.
Bibliography
[1] J. Nicholas Laneman and Gregory W. Wornell. Energy-efficient antenna sharing and relaying for wireless networks. In Proc. IEEE Wireless Comm. and Networking Conf. (WCNC), Chicago, IL, September 2000.
[2] Thomas M. Cover and Cyril S.K. Leung. An achievable rate region for the multiple- access channel with feedback. IEEE Trans. Inform. Theory, 27(3):292–298, May 1981.
[3] Frans M.J. Willems and Edward C. van der Meulen. The discrete memoryless multiple- access channel with cribbing encoders. IEEE Trans. Inform. Theory, 31(3):313–327, May 1985.